30 - Cyber Attack
Cyber Attack is an assault launched by cybercriminals using one or more computers against a single or multiple computers or networks. A cyber attack can maliciously disable computers, steal data, or use a breached computer as a launch point for other attacks. Among others, methods to launch cyber attack can be malware, phishing, ransomware, or denial of service.
Should we use term Cybercriminals?
Currently, we constantly use the terms such as black hat, hacker, or cracker. Should we rather talk about cybercriminals? Usually the media uses the term hacker, and this does not tell the whole truth whether a hacker is good or bad. From the author’s perspective, we should use the term cybercriminals because they break the law! Yes, I know there is a term black hat hacker, but why don’t we give the (honorary) title to someone who really is a cybercriminal?
Cyber Landscape
The landscape is constantly changing and staying up to date is challenging today. The best way to stay up to date is to keep track of current reports from cyber companies. However, it must be remembered that companies always inform of the figures from their own point of view, and therefore these figures must be read critically.
-
Tip #1 – Data Sources: For example, a vendor claims that 85% of all systems have been successfully infected by a particular family of malware. However, when you dig into the source of the data used to make this claim, it turns out that 85% of systems using the vendor's online malware cleaner website were infected with the malware referenced. Notice that "85% of all systems" is a dramatic extrapolation from "85% of all systems that used their online tool.“
-
Tip #2 – Time Periods: Let's say a vendor is reporting on how many vulnerabilities were disclosed in their products for a given period. If the data is reported in regular sequential periods of time, such as quarterly, the trend looks really bad as large increases are evident. But instead of reporting the trend using sequential quarterly periods, the trend looks much better when comparing the current quarter to the same quarter last year; there could actually be a decrease in vulnerability disclosures in the current quarter versus the same quarter last year. This puts a positive light on the vendor, despite an increase in vulnerability disclosures quarter over quarter.
-
Tip #3 – Recognizing Hype: For example, a threat intelligence vendor publishes data that claims 100% of attacks in a specific time period involved social engineering or exploited a specific vulnerability. The problem with such claims is that no one in the world can see 100% of all attacks, period.
Enisa Threat Landscape 2020
Enisa published Threat Landscape report in October 2020. This publication is divided into 22 different reports, available in pdf and eBook formats. The combined report lists the major change from the 2018 threat landscape as the COVID-19-led transformation of the digital environment. During the pandemic, cyber criminals have been seen advancing their capabilities, adapting quickly, and targeting relevant victim groups more effectively.
EU Agency for Cybersecurity Executive Director Juhan Lepassaar said: “Cyber threats are evolving and becoming increasingly complex. This is not new. The Agency has developed the latest ‘ENISA Threat Landscape’ into a more user-friendly format meeting the needs of its beneficiaries who can use it to advance their readiness and target the response better.”
ENISA Threat Landscape: 15 Top Threats in 2020
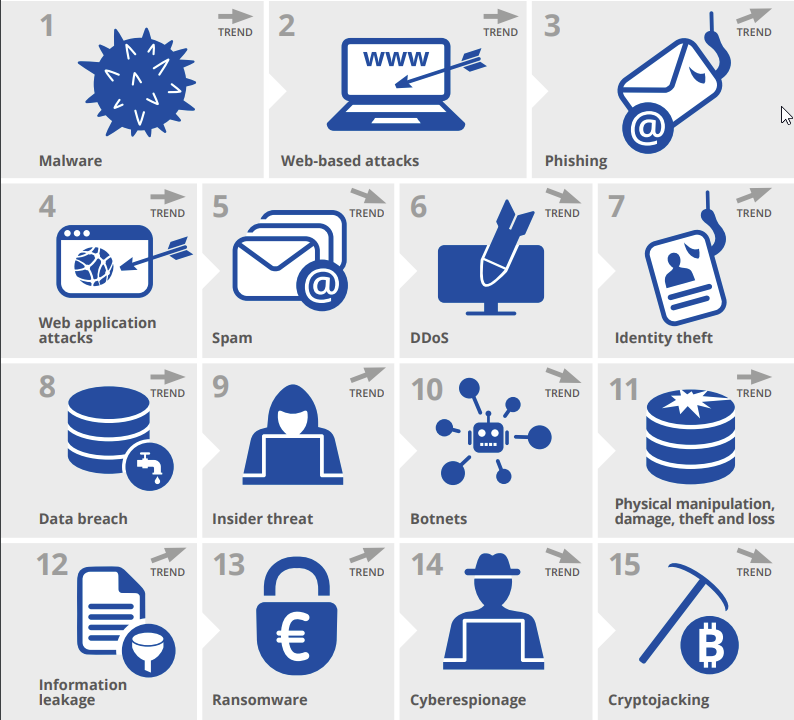
- Malware
- Malware is a common type of cyber attack in the form of malicious software. Families of malware include cryptominers, viruses, ransomware, worms and spyware. Its common objectives are information or identity theft, espionage and service disruption
- Web-based Attacks
- Web-based attacks are an attractive method by which threat actors can delude victims using web systems and services as the threat vector. Example malicious content on webpage, compromised webpage, steal information.
- Phishing
- Phishing is the fraudulent attempt to steal user data such as login credentials, credit card information, or even money using social engineering techniques. This type of attack is usually launched through e-mail messages, appearing to be sent from a reputable source, with the intention of persuading the user to open a malicious attachment or follow a fraudulent URL.
- Web Application Attacks
- Web applications and technologies have become a core part of the internet by adopting different uses and functionalities. Attack can target by example content management system or SQL database or XSS cross site scripting.
- SPAM
- Receiving spam is an inconvenience, but it may also create an opportunity for a malicious actor to steal personal information or install malware. Spam consists of sending unsolicited messages in bulk. It is considered a cybersecurity threat when used as an attack vector to distribute or enable other threats.
- Distributed Denial of Service (DDoS)
- Distributed Denial of Service (DDoS) attacks are known to occur when users of a system or service are not able to access the relevant information, services or other resources.
- Identity Theft
- Identity theft or identify fraud is the illicit use of a victim’s personal identifiable information (PII) by an impostor to impersonate that person and gain a financial advantage and other benefits.
- Data Breach
- A data breach is a type of cybersecurity incident in which information (or part of an information system) is accessed without the right authorisation, typically with malicious intent, leading to the potential loss or misuse of that information.
- Insider Threat
- An insider threat is an action that may result in an incident, performed by someone or a group of people affiliated with or working for the potential victim.
- Botnets
- A botnet is a network of connected devices infected by bot malware. These devices are typically used by malicious actors to conduct Distributed Denial of Service (DDoS) attacks
- Physical Manipulation, Damage, Theft and Loss
- As the title suggests, this means Physical Manipulation, Damage, Theft and Loss. The integrity of devices is vital for technology to become mobile and for most implementations of the Internet of Things (IoT). Remember also smart sensors, Wi-Fi cameras, smart security lighting, drones and electronic locks
- Information Leakage
- A data breach occurs when data, for which an organization is responsible, is subject to a security incident resulting in a breach of confidentiality, availability, or integrity. A data breach frequently causes an information leakage, which is one of the major cyber threats, covering a wide variety of compromised information from personal identifiable information, financial data stored in IT infrastructures to personal health information kept in healthcare providers’ repositories.
- Ransomware
- Ransomware has become a popular weapon in the hands of malicious actors who try to harm governments, businesses and individuals on a daily basis. In such cases, the ransomware victim may suffer economic losses either by paying the ransom demanded or by paying the cost of recovering from the loss, if they do not comply with the attacker’s demands
- Cyber Espionage
- Cyber espionage is considered both a threat and a motive in the cybersecurity playbook. It is defined as ‘the use of computer networks to gain illicit access to confidential information', typically that held by a government or other organization
- Cryptojacking
- Cryptojacking (also known as cryptomining) is the unauthorized use of a device’s resources to mine cryptocurrencies. Targets include any connected device, such as computers and mobile phones; however, cybercriminals have been increasingly targeting cloud infrastructures.
Recommendations
Enisa's reports are recommended reading. In these reports, you can find commentary on Kill Chain viewpoint, what today’s trends are, how to mitigate threats and wide references list!
Other reports
These reports can be found on the internet by their search terms: Security report, Threat report, Internet security threat report. Or just visit known security companies’ pages and look for White papers or Resources pages. A few links are listed below:
- Sophos 2020 Threat Report (pdf)
- Fortinet Global Threat Landscape Report 2020 (pdf)
- McAfee Labs COVID-19 Threats Report (pdf)
- Panda Security Threat Insights Report 2020 (pdf)
- Fireeye M-Trends 2020 (pdf)
- Accenture Cyber Threatscape report 2020 (pdf)
- Checkpoint Cyber Security Report 2020 (pdf)
- Sonicwall Cyber Threat Report 2020 (pdf)