33 - Intrusion methods
Previous chapter went through kill chain and attack matrix. In this chapter, the main topic is intrusion methods. Before we can go into intrusion phase, we need reconnaissance and after that, a possible intrusion.
- Attacker is making reconnaissance, identifying targets and tactics for the attack
- Based on what the attackers discovered in the reconnaissance phase, they’re able to get into your systems
- Often leveraging malware or security vulnerabilities.
Example once you have gained the intel, it is time to break in. Intrusion is when the attack becomes active: attackers can send malware (ransomware, spyware, adware) to the system to gain entry. This is the delivery phase: it could be delivered by phishing email; it might be a compromised website. Intrusion is the point of entry for an attack, getting the attackers inside.
Kill chain model helps us to identify the stages of different threats and what each belongs to. For example Enisa Phishing report 2020 shows that phishing belongs to Reconnaissance, Weaponization, and Delivery steps in the kill chain model.
Source: https://www.enisa.europa.eu/publications/phishing
This can be visualized in many ways and Varonis has done a great job with this. Each phase of the kill chain is an opportunity to stop a cyberattack in progress: with the right tools to detect and recognize the behavior of each stage, you are able to better defend organization against a system or data breach.
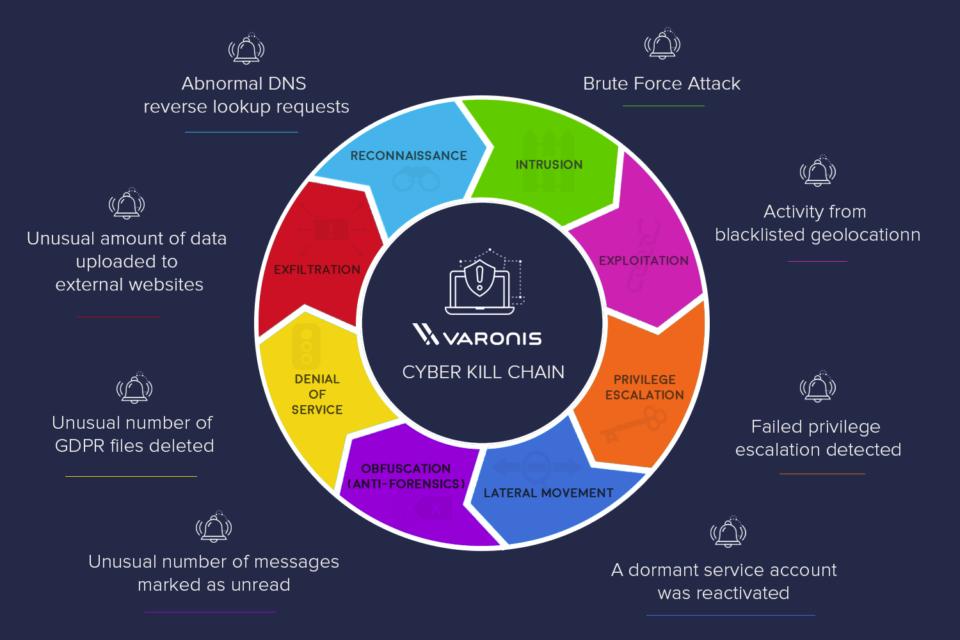
Varonis article "What is The Cyber Kill Chain and How to Use it Effectively" is recommended reading.
Source: https://www.varonis.com/blog/cyber-kill-chain/
Mitre ATT&CK TTP
ATT&CK has become a valuable resource for organizations who wish to have a better understanding about specific threats they may face. ATT&CK tracks and profiles past and current adversary threats so organizations can understand specific TTPs.
Tactics: The MITRE ATT&CK Matrix contains 12 columns representing enterprise tactics leveraged by cybercriminals. These represent the “why” of a technique and describe what an adversary is trying to accomplish. In general, it is a tactical objective and the reason behind the action.
Techniques: The rows in the MITRE ATT&CK matrix are the techniques leveraged to perform the action for a specific tactic. In general, a technique represents how the threat actor achieves a tactical objective.
Procedures: By clicking a specific technique, the MITRE ATT&CK matrix will present the detailed information on how an adversary would implement the technique to achieve an objective. MITRE also provides examples of procedures based on past and known attacks.
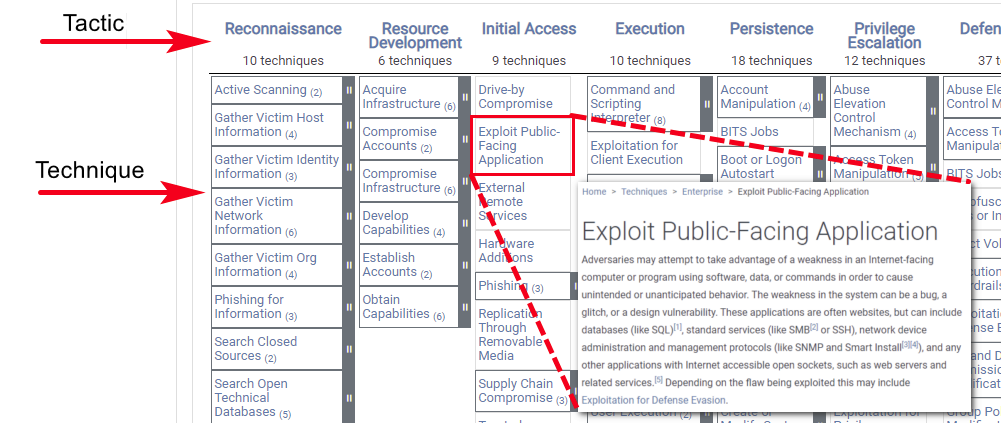
Source: https://security.radware.com/ddos-experts-insider/hackers-corner/tactics-techniques-procedures/
Mitre ATT&CK TTP Example
With Mitre Navigator it is possible to combine different attack vectors and find out what the tactics on these attacks are. Below the figure shows an example where APT28 and APT33 have been combined showing what the vectors are.
For example, if we select "T1080 Exploitation for Privilege Escalation", the navigator shows score 2. This means that both APT28 and APT33 use this. Now we can look at the tactics and techniques. With this information we can plan how to defend these groups.

If you want to make your own Mitre model on Navigator, here is good example how to do this: https://security.radware.com/ddos-experts-insider/hackers-corner/tactics-techniques-procedures/
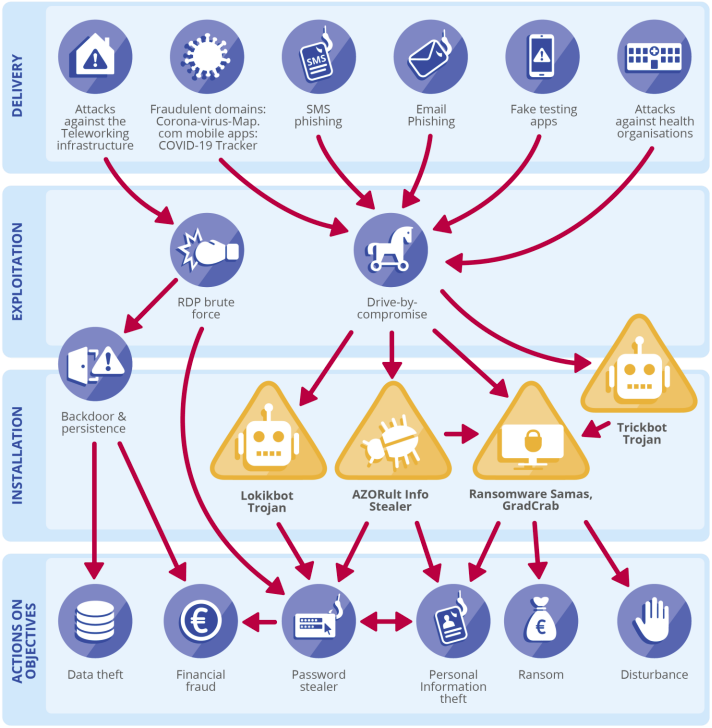
Enisa threat landscape mapping
Enisa has analyzed threats during COVID-19 pandemic period and has made a visual chart. "Exploitation by cybercriminals and advanced persistent threat (APT) groups of the current coronavirus (COVID-19) global pandemic". The graph shows what the delivery methods are, how these exploit and install, and what the action objectives are.