61 - What is a cyber exercise
Cyber security exercises provide opportunities for organizations to demonstrate critical capabilities and reveal how effectively they integrate people, processes, and technology to protect their critical information, services, and assets. The exercises can help train organizations to improve their ability to mitigate impacts to business from cyber threats and attacks.
NIST SP 800-84 defines that exercise is a simulation of an emergency designed to validate the viability of one or more aspects of an IT plan. In an exercise, personnel with roles and responsibilities in a particular IT plan meet to validate the content of a plan through discussion of their roles and their responses to emergency situations, execution of responses in a simulated operational environment, or other means of validating responses that do not involve using the actual operational environment. Exercises are scenario-driven, such as a power failure in one of the organization’s data centers or a fire causing certain systems to be damaged, with additional situations often being presented during the course of an exercise. There are several types of exercises, and this publication focuses on the following two types that are widely used by single organizations in TT&E programs:
-
Tabletop Exercises. Tabletop exercises are discussion-based exercises where personnel meet in a classroom setting or in breakout groups to discuss their roles during an emergency and their responses to a particular emergency situation. A facilitator presents a scenario and asks the exercise participants questions related to the scenario, which initiates among the participants a discussion about roles, responsibilities, coordination, and decision-making. A tabletop exercise is discussion-based only and does not involve deploying equipment or other resources.
-
Functional Exercises. Functional exercises allow personnel to validate their operational readiness for emergencies by performing their duties in a simulated operational environment. Functional exercises are designed to exercise the roles and responsibilities of specific team members, procedures, and assets involved in one or more functional aspects of a plan (e.g. communications, emergency notifications, IT equipment setup). Functional exercises vary in complexity and scope, from validating specific aspects of a plan to full-scale exercises that address all plan elements. Functional exercises allow staff to execute their roles and responsibilities as they would in an actual emergency situation but in a simulated manner.
About Cyber Security Exercises Terminology
Please note that the global terminology on Cyber Security Exercises is not fully agreed. In FlagsShip 1 the terminology described in “Pedagogical Aspects of Cyber Security Exercises” by Karjalainen, Kokkonen and Puuska is followed. As an example, the used terminology differs from the terminology that the National Cyber Security Centre of Finland (NCSC-FI) uses chapter 62 - Cyber exercise scenarios: NCSC-FI uses the term Scenario that in FlagShip 1 model maps to an Event. The figure from the before mentioned publication shows the relationship of Scenario - Operation - Event - Inject.
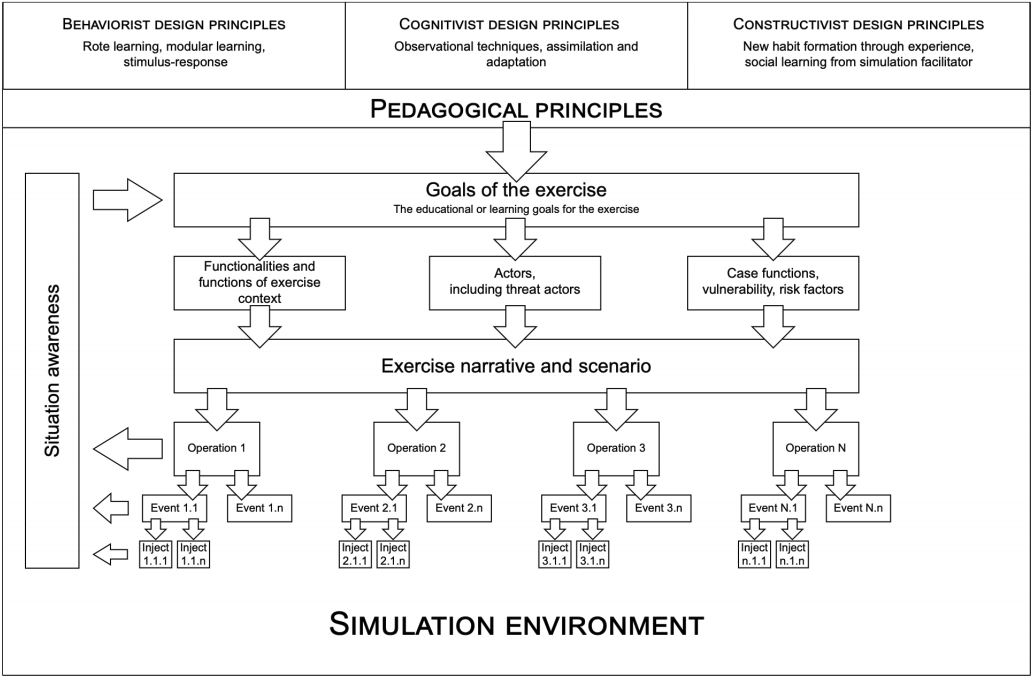
Download: Review of Pedagogical Principles of Cyber Security Exercises
Other exercise examples
Live exercise is an exercise that is based on real events to increase the realism on selected scenario. The exercise includes an active adversary team (Red Team) that conducts objective campaign against exercise training audience. Live exercises often include multiple organizations (i.e. service providers, subcontractors, internal and external partners) that depend on each other for providing business services. Live exercises are planned together with the customer to provide a realistic and suitable exercise scenario.
Digital Forensics and Incident Response (DFIR) exercise is an exercise where training audience needs to investigate a cyber-attack that already happened. DFIR exercise is especially constructed for technical specialists, IT managers, and Security managers to learn how to identify different indicators of compromise and conduct incident management and incident response. DFIR exercise is a great tool for organizations to test and evaluate their capabilities on conducting incident response within the organization or in collaboration with their service provider.
Blue Team CTF is a threat hunting exercise where the focus is to find and analyze threat actor’s activities in a gamificated scenario. The training audience investigates traces of a multi-phase cyber attack from different organization environments. The aim of the exercise is to analyze the different flags and other traces and create timeline and attacker’s activity mapping. The participants learn how to hunt threat actors in different environments and how attackers conduct their campaigns and TTPs (Tactic, Techniques, Procedures). During the exercise, the scenarios are thoroughly reviewed including the attacking methods, tools, and how defenders can find the traces of the attacks.
Related materials
- ECSO - Understanding Cyber Ranges: From Hype to Reality, 2020 (pdf)
- TRAFICOM - Instructions for organising cyber exercises
- Vatanen, M. - Requirements for technical environment of cyber security exercises
- CS4E - WP 7.1 - Report on existing cyber ranges, requirements, p.49-65
- Karjalainen, M. & Kokkonen T. Review of Pedagogical Principles of Cyber Security Exercises
- Mitre: Finding Cyber Threats with ATT&CK™-Based Analytics (pdf)