53 - Risk Management
The Risk Management Framework (RMF), presented in NIST SP 800-37, provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.
The process of managing risks to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the nation, resulting from the operation of an information system, and includes: (i) the conduct of a risk assessment; (ii) the implementation of a risk mitigation strategy; and (iii) employment of techniques and procedures for the continuous monitoring of the security state of the information system.
Risk assessment can be performed in many different ways, but usually in cyber security the main thing is calculating or priorization the risk. The easiest way to do this is to use likelihood and consequences table. Below is an example of a 3x3 grid.
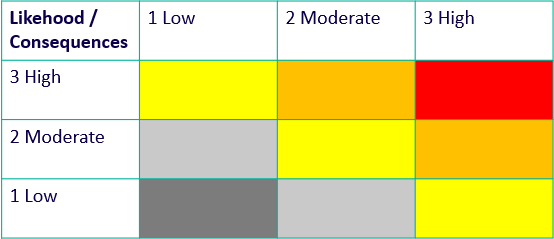
Not applicable = Not included
1. Low = Noticeable impact
2. Moderate = Significant damage
3. High = Critical damage
For example: Staff computer and possible ransomware on email attachment = Likelihood could be 1 (Low) and Impact could be 3 (High). So probably a staff person doesn't click on this ransomware because he/she knows what would happen and that is why the likelihood is low. Impact is High because if ransomware encrypt files damage would be significant!
Risk management can also be used as an example for how much money you should use to protect any device.
1) Employee loses a computer
Computer value 600 €
Work interruption 3 days, one person, 1200 €
Likelyhood once in a year
Personal data, commercial data, customer data; intolerable
In the example case above the costs are 1800€ and the likelihood is one year. So now we know how much this costs (if it happens), so it would be easier to justify the owner that if we use 10% of these costs to protect computers, it’s still reasonable. Another example could be likelihood once in three years. From the yearly rate i.e. 1800€ divided by 3 we could use 600€ to protect the computer.
There is also Mitre 5x5 grid model. The method is the same, but the evaluation is wider than in the previous model. More information can be found at MITRE: Risk mitigation planning, implementation and progress monitoring.
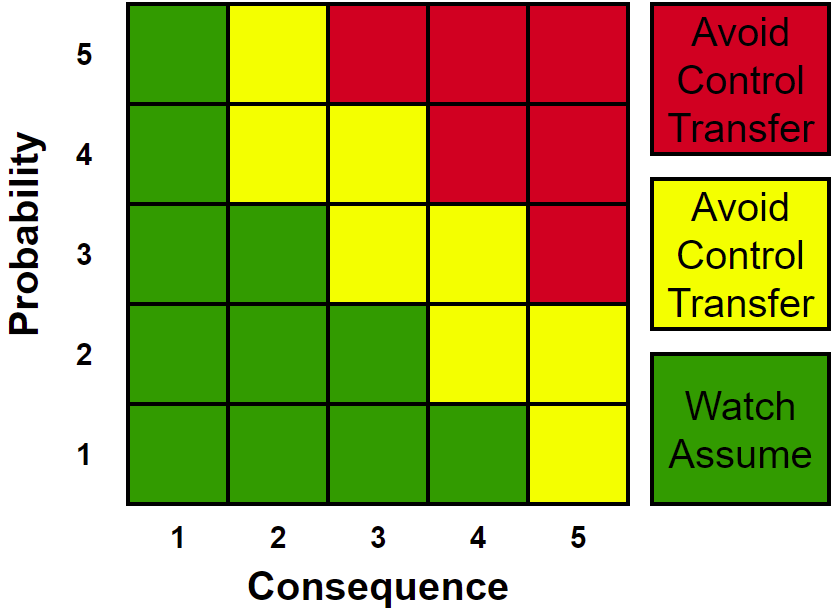
Risk mitigation handling options include:
- 1. Assume/Accept: Acknowledge the existence of a particular risk and make a deliberate decision to accept it without engaging in special efforts to control it. An approval of project or program leaders is required.
- 2. Avoid: Adjust program requirements or constraints to eliminate or reduce the risk. This adjustment could be accommodated by a change in funding, schedule, or technical requirements.
- 3. Control: Implement actions to minimize the impact or likelihood of the risk.
- 4. Transfer: Reassign organizational accountability, responsibility, and authority to another stakeholder willing to accept the risk.
- 5. Watch/Monitor: Monitor the environment for changes that affect the nature and/or the impact of the risk.