54 - Flagship 1 Task
Reminder: This training part is based on research and what should be fixed (mitigation and remediation). This is not directly related to the Flagship 1 exercise.
On chapter 52 - Auditing methods we went through examination techniques. After examination the next step would be target Identification and analysis. One way to do this is to use OpenVAS and Nessus vulnerability scanners. Both are commercial products, but they also offer a free/test version with limited functionality.
It usually takes a few hours’ time to install (and update) these programs, so we have completed the scan already. Please see through the scan results. This scan result is a good example on the fact that vulnerability scanners do not find everything.
Nessus scan to Kybereo machine
CS4E-01-Nessus-Advanced_Custom_report.pdf
Reminder: Vulnerability scanners can find only known vulnerabilities, if program/service provider has a built plugin which will recognize this vulnerability. These are good, automated tools, but you cannot trust them to find everything possible!
Task 01: Open Nessus scan report and find some CVE vulnerability codes. Open webpage https://nvd.nist.gov/vuln/search and find out more information on these vulnerabilities
Task 02: Open Nessus scan report and find some CVSS score results. Open webpage https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator and try to import these results on a calculator (Example: AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N). Did you get the same score? Look through what each value means (hint: move mouse cursor over the text on your calculator and it shows the information).
NMAP
Nmap ("Network Mapper") is a free and open source utility for network discovery and security auditing. This tool can be found on Kali and it is a command line based tool. More information can be found on https://nmap.org/
Task 03: Start both (Kali + Kybereo) virtual machines and log in on Kali. Open terminal, test the commands below and find out what the results mean. Try to find out some other nmap commands and also test them.
- nmap -iflist
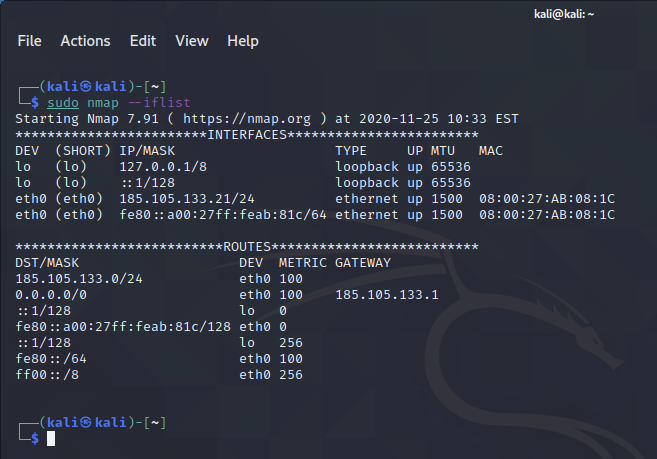
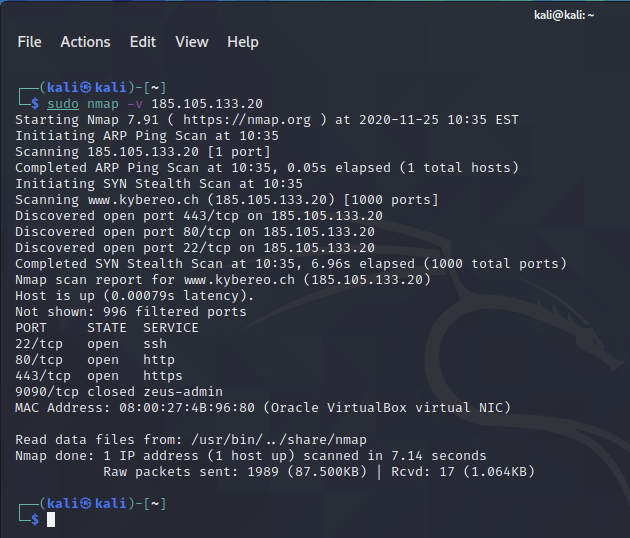
- nmap -v KYBEREO-IP-ADDRESS
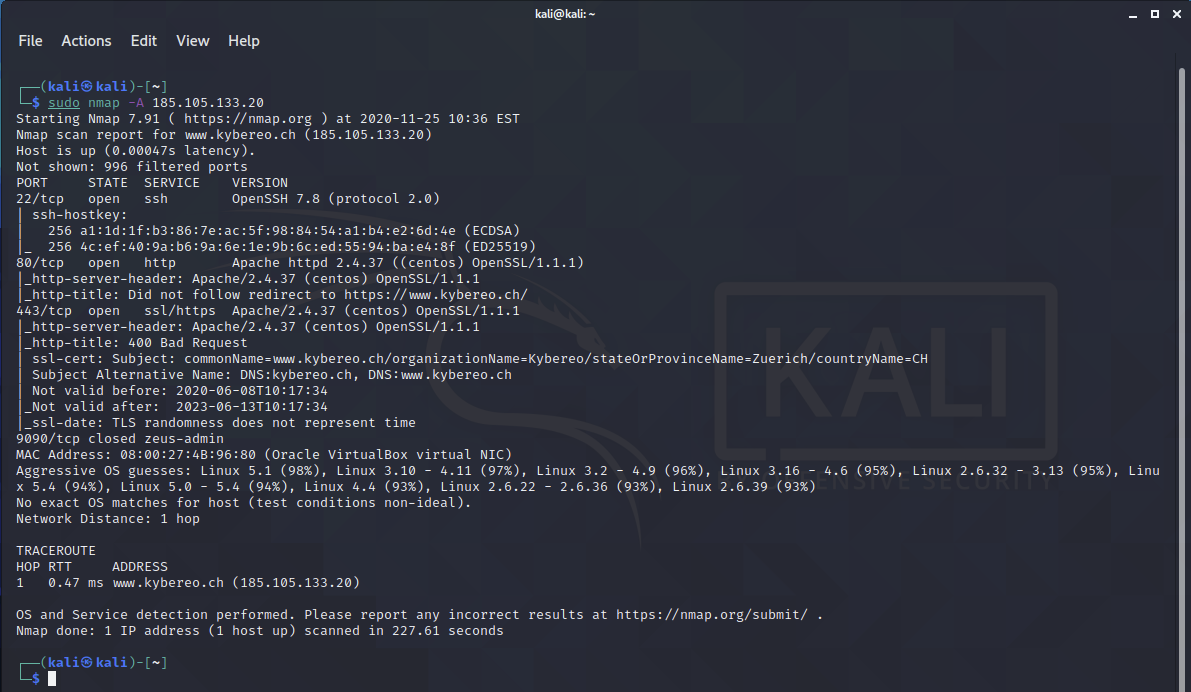
- nmap -A KYBEREO-IP-ADDRESS
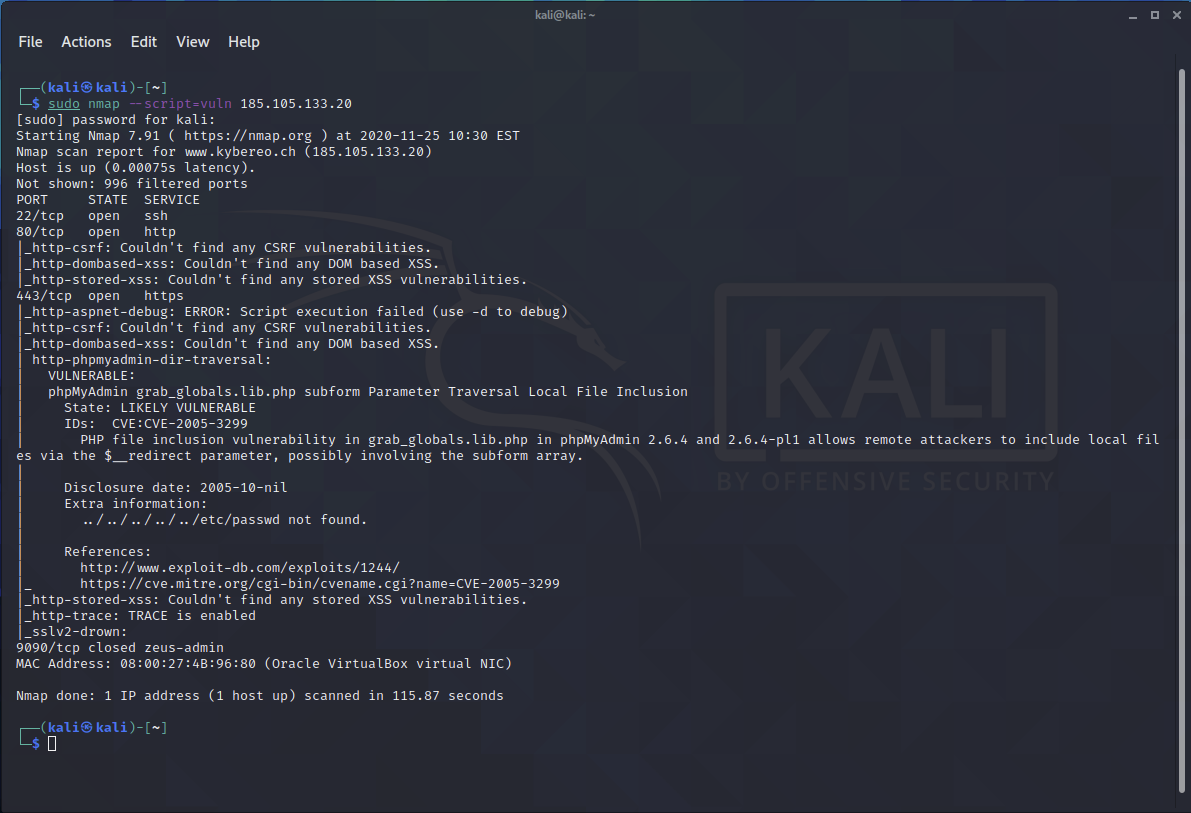
- nmap --script=vuln KYBEREO-IP-ADDRESS
nmap -iflist (click this to see example)
nmap -v (click this to see example)
nmap -A (click this to see example)
nmap --script=vuln (click this to see example)
Task 04: Test the commands below. Find out what is the difference between these two. What information did you get with these commands?
- nmap -p 80 -A KYBEREO-IP-ADDRESS
- nmap -p 443 -A KYBEREO-IP-ADDRESS
nmap -p 443 -A (click this to see example)
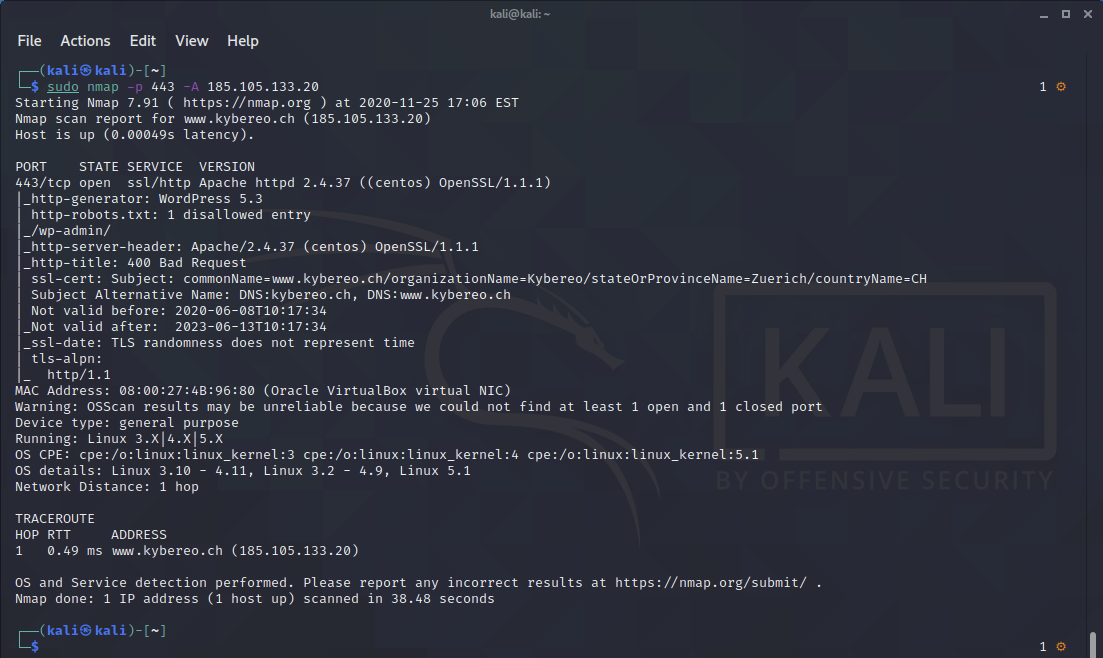
CPE
Common Platform Enumeration is one way to research known vulnerabilities on a specific software.
Task 05: On task 04. we found out Kybereo WordPress and Apache version. Use CPE and find out what vulnerabilities this version compared to the latest includes. Are there some critical vulnerabilities?