54 - Known vulnerabilities
A vulnerability is a weakness or error in a system or device’s code that, when exploited, can compromise the confidentiality, availability, and integrity of data stored in them through unauthorized access, elevation of privileges, or denial of service.
Exploit is a technique to breach the security of a network or information system in violation of security policy. Usually it can also be explained as a code or tool used to take advantage of a vulnerability.
Most of the disclosed vulnerabilities are shared on the National Vulnerability Database (NVD) and enumerated in the Common Vulnerabilities and Exposures (CVE) List to make it easier to share data across separate vulnerability capabilities. With this database, we can search for more information on different vulnerabilities and how to fix them.
The goal of CVE is to make it easier to share information about known vulnerabilities across organizations. CVE does this by creating a standardized identifier for a given vulnerability or exposure. CVE identifiers or CVE names allow security professionals to access information about specific cyber threats across multiple information sources using the same common name.
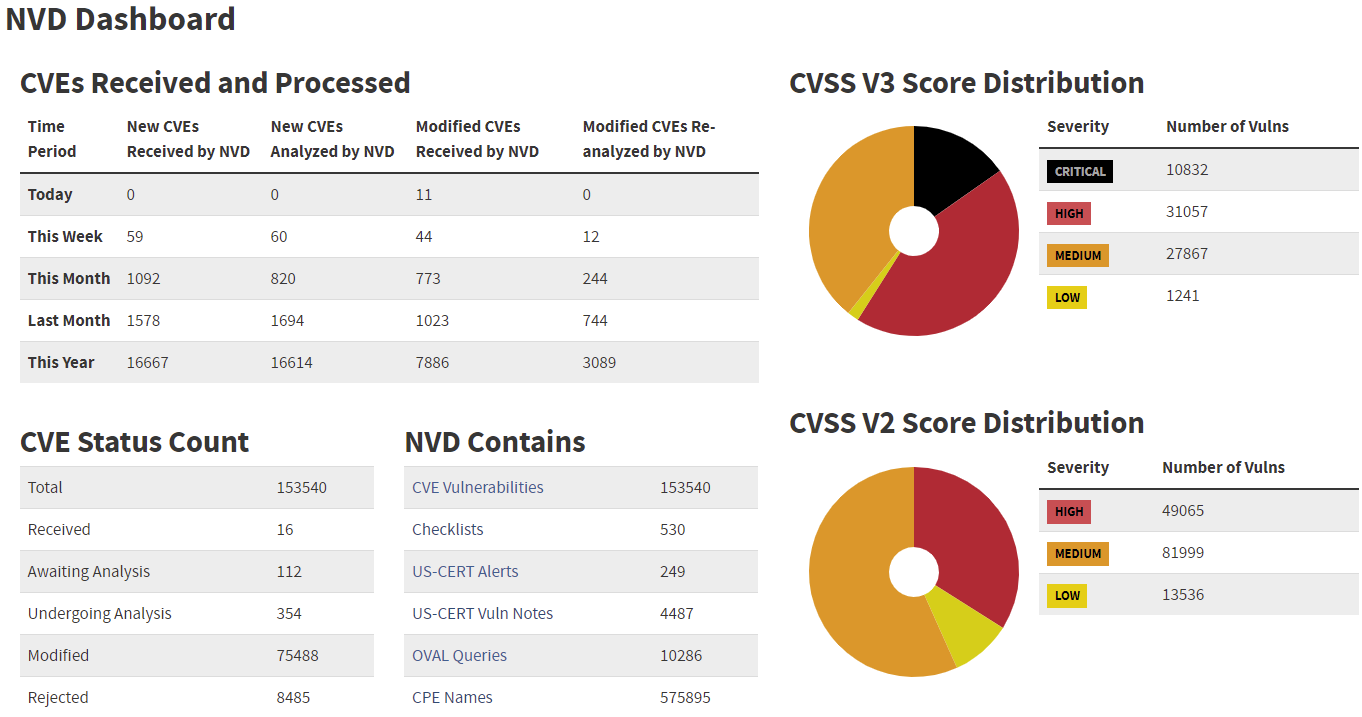 Figure: 24.11.2020, https://nvd.nist.gov/general/nvd-dashboard
Figure: 24.11.2020, https://nvd.nist.gov/general/nvd-dashboard
CPE - Common Platform Enumeration
The Common Platform Enumeration (CPE), according to http://cpe.mitre.org/, is essentially a standardized method of describing and identifying various classes of applications, operating systems, and hardware devices within an organization’s overall computing assets. Additionally, CPE can be effectively utilized as a source of information for enforcing and verifying IT management policies as it relates to assets, such as vulnerability, configuration, and remediation policies, etc.
More information: https://nvd.nist.gov/products/cpe
CVE vs. CPE
Both are good tools, but the viewpoint is different. CVE focuses on vulnerabilities whereas CPE focuses on what vulnerabilities are found in example application version.
Example 01. CVE-2008-4250. This site provides information about that vulnerability, what it does and how it can be fixed.
Example 02. cpe:2.3:o:microsoft:windows_xp:-:sp2:::professional::x64: Link to CPE summary page, what are the vulnerabilities on this version. This site provides information about all vulnerabilities which affect the operating system (Windows XP, SP2, Pro 64bit)
Example 03. If your company maintains a webserver with Apache 2.4.10, we can make CPE search and find out all vulnerabilities targeted from this version onwards. This is an easier way to find out vulnerabilities without using a scanning tool.
Vulnerability Metrics
There are multiple ways to evaluate the severity of a vulnerability. One is the Common Vulnerability Scoring System (CVSS), a set of open standards for assigning a number to a vulnerability to assess its severity. CVSS scores are used by the NVD, CVE and others to assess the impact of vulnerabilities. Scores range from 0.0 to 10.0, with higher numbers representing a higher degree of severity of the vulnerability.
CVSS is composed of three metric groups: Base, Temporal, and Environmental, each consisting of a set of metrics
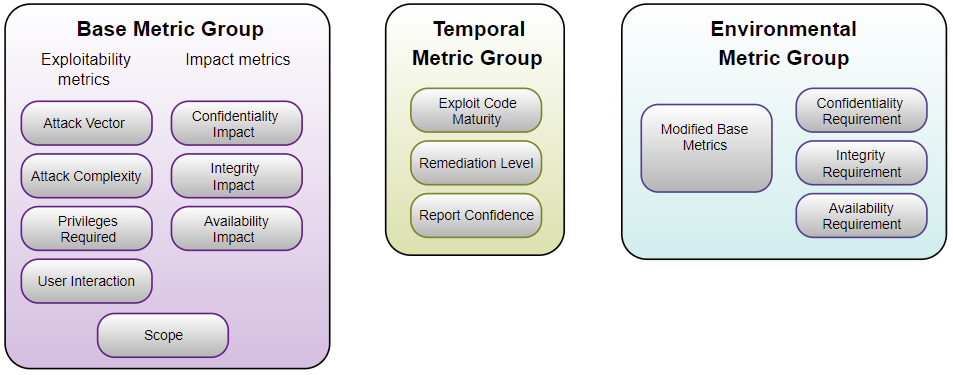
The Base metric group represents the intrinsic characteristics of a vulnerability that are constant over time and across user environments. It is composed of two sets of metrics: the Exploitability metrics and the Impact metrics.
The Exploitability metrics reflect the ease and technical means by which the vulnerability can be exploited. That is, they represent characteristics of the issue that is vulnerable, which we formally refer to as the vulnerable component. The Impact metrics reflect the direct consequence of a successful exploit and represent the consequence to the thing that suffers the impact, which we formally refer to as the impacted component.
The Temporal metric group reflects the characteristics of a vulnerability that may change over time but not across user environments. For example, the presence of a simple-to-use exploit kit would increase the CVSS score, while the creation of an official patch would decrease it.
The Environmental metric group represents the characteristics of a vulnerability that are relevant and unique to a particular user’s environment. Considerations include the presence of security controls which may mitigate some or all consequences of a successful attack, and the relative importance of a vulnerable system within a technology infrastructure.
Source: CVSS Specification document
Example: CVSS 3.1 base score was 7.8 (CVSS v3.1 Vector AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) See example with explanations